Questions & Answers
What is GATE-Ware?
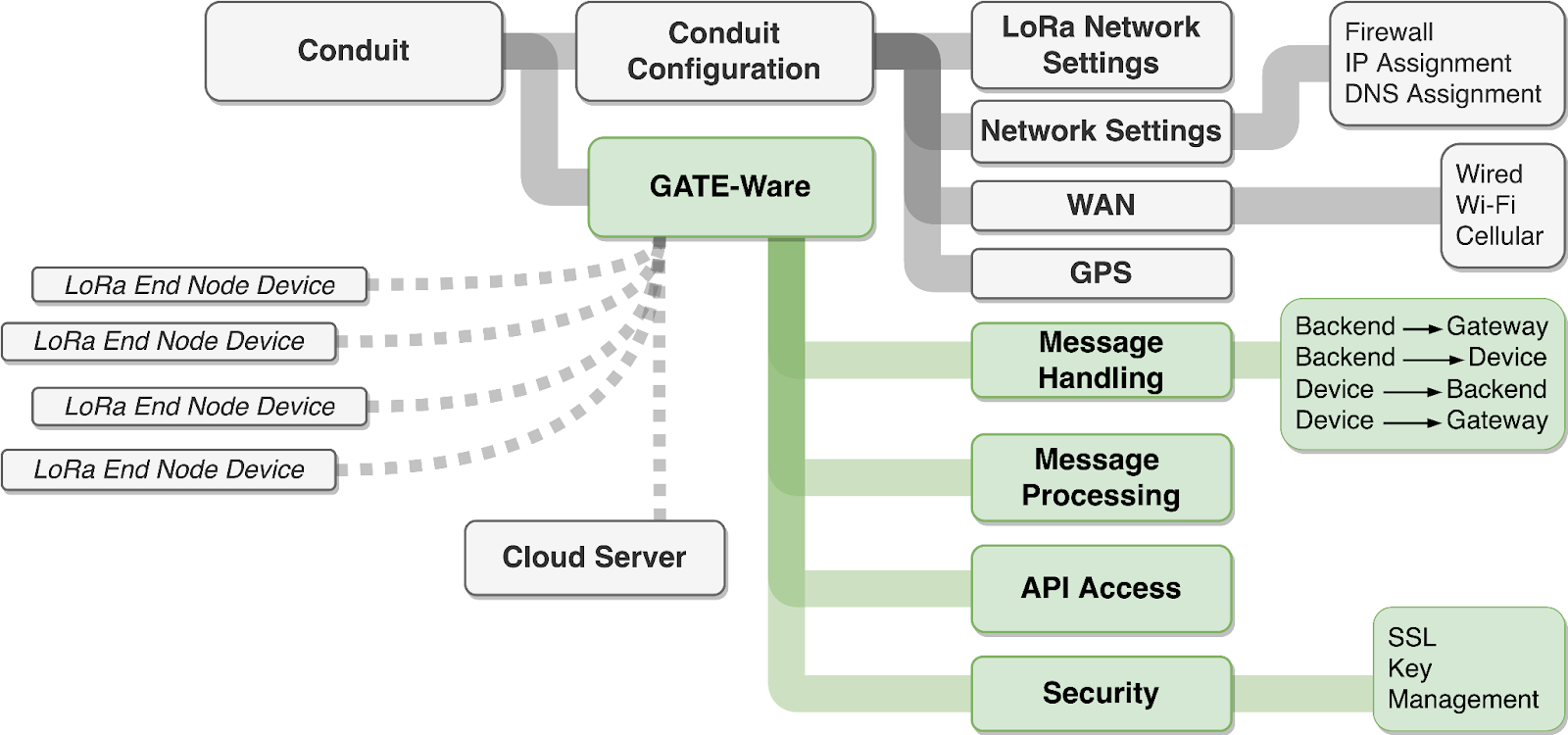
GATE-Ware is an application that connects your Conduit to your cloud within 5 minutes of unboxing.
The application is designed to be a complete solution for cloud integration, device management, and edge processing leveraging LoRaWAN.
What do you mean “connects?”
Your freshly-unboxed Conduit will:
- Create a broker connection to your cloud via MQTT over TLS.
- Transmit data via MQTT from new and existing LoRaWAN end nodes to your cloud.
- Expose MultiTech’s complete mPower API to your cloud via MQTT - for complete remote management.
- Exercise a pass-through example edge processing routine, which you can then modify with your own logic.
All within 5 minutes.
GATE-Ware takes the form of a standard MultiTech Custom Application, deployable remotely (DeviceHQ or VPN) or locally.
You can convert your already field-deployed Conduits to using GATE-Ware within minutes.
What cloud does it communicate with?
We support standard MQTT on any cloud. This includes AWS IoT Core, Azure IoT Hub, and Azure IoT Central.
Is configuration part of the 5 minutes?
Yes, GATE-Ware’s configuration file is hyper-simple. Just drop your cloud’s endpoint and credentials into a centralized json configuration, then GATE-Ware does the rest.
Later you can revisit the configuration file and extend functionality.
Are there recurring fees?
None. A one-time license key is all you need to purchase, then a major versioned copy of GATE-Ware is yours for eternity.
The GATE-Ware team believes that LoRaWAN should not be treated as a Telco or a SaaS.
What about data privacy?
GATE-Ware is privacy by design, in that data is securely transferred to your cloud, without involving third parties. The application supports MQTT over TLS. GATE-Ware never sends your data anywhere but to your configured endpoint.
Can I customize GATE-Ware?
Yes, via our easy to use edge-processing frameworks, you can modify, route and even discard data from LoRaWAN end nodes - we’ve found this to be very desirable for selectively transmitting data via costly cell links. Unlike SaaS providers, GATE-Ware transmits only what you want you send, to your endpoint only.
How restrictive are the edge frameworks?
As long as the Conduit’s Linux will run it, and it adheres to the very basic data I/O requirements of GATE-Ware, then you can write your edge processing logic in whatever language you wish.
We provide examples in Python and Bash.
GATE-Ware introduces nothing proprietary and no funky custom languages or schemas.
Who was GATE-Ware made for?
We made GATE-Ware for ourselves at first! Three Labs grew as a consulting business and has deployed MultiTech-based LoRa solutions for clients for several years.
Initially, we were seeking a method for reducing our own engagement and development overhead:
“If we could just spin up each of these engagements in 5 minutes..”
Ultimately the wish became a reality as we designed our very own version of what we wanted from a LoRa application framework.
We decided to package GATE-Ware for end users, along with several features missing from the LoRaWAN SaaS market leaders, like:
- Edge processing, via what we call “Transforms.”
- Privacy by design - your data is truly your data. We have no special hooks or requirements… or even servers for consuming any of your data.
- A One-time license fee! We realize that this is virtually unheard of, but made possible because we don’t have to incur the costs of ingesting your data.
- Hyper focus on maintaining minimal complexity - GATE-Ware’s config file is a one-stop shop and simple.
GATE-Ware is our very own custom application. We use the exact same product that we make available to customers for end use.
What else should I consider?
Whether you choose GATE-Ware or a SaaS, you haven’t escaped the responsibilities of owning and maintaining the physical LoRaWAN network.
Fortunately, GATE-Ware can assist you with the responsibilities below in ways that a SaaS typically does not:
-
Deploying the network properly and ensuring link health (i.e. placement and transmission path of Conduit and end devices):
- We’ve created some best practices guides for our customers. If you’d like additional help, Three Labs can provide consultation.
-
Paying for data to/from the Conduit (especially on Cellular):
- Reduce data costs by transmitting only interesting data, using edge processing.
-
Running a cloud for your own business logic:
- Reduce compute costs by installing logic in the Conduit and having no third party SaaS costs.
-
Managing your Conduit’s health:
- GATE-Ware exposes the complete MultiTech mPower interface, providing full remote configuration. No VPN or local access to the conduit is required.
How do I get started?
‘Getting started’ is easy, and may be all that you need to do if data pass-through and mPower access is all that you need. Head over to the section linked below to quickly complete your setup:
> Click here to visit the Getting Started page
GATE-Ware encourages the use of edge processing:
If you wish to create business logic for acting on your data before transmission, you’ll be able to do so via GATE-Ware’s “Transform” functionality. Head over to the section linked below to see examples and make use of edge processing features.
> Click here to visit the Transforms page
We encourage you to take a complete tour of the GATE-Ware documentation, as we try to keep it simple and effective.
Please do not hesitate to reach out directly if there’s something that we can helop clarify, or something additional that you’d like to see: info@threelabs.io.
Getting Started
1. Complete Pre-Installation Requirements
The requirements below are the base components and infrastructure that one needs for before setting up and running the GATE-Ware application.
- Your Conduit must be connected and initial configuration steps according to Multitech’s instructions here.
- You must have the GATE-Ware distribution on your computer. *
- You must have a valid GATE-Ware license. *
- The backend (AWS, Azure or MQTT) must be configured and credentials generated according to the provider’s instructions. GATE-Ware can be run without cloud TLS credentials, but they are strongly recommended.
* For software distributions and licenses, please request an evaluation license at eval.gateware.io or contact us directly at support@threelabs.io.
2. Create a Configuration File
Whether you choose a cloud provider or roll-your-own offline solution, GATE-Ware has you covered with appropriate with “base configurations” for each scenario.
Base configuration step-by-step:
A “base configuration” is nothing more than the minimum set of configuration attributes required by GATE-Ware. For complete information on all configuration options, please see the Attributes section.
- Identify your cloud below (or custom/roll-your-own MQTT).
- Cut and paste the associated JSON content into a new file named:
gateware.json.
- Replace the example credentials, endpoint, port and license key with your cloud-specific and purchased key values.
MQTT - Including AWS IoT Core
Click to Expand gateware.json: MQTT Broker - TLS with Client Certificate Authentication
{
"backend_mqtt_ca": "-----BEGIN CERTIFICATE-----\n...\n-----END CERTIFICATE-----",
"backend_mqtt_client_cert": "-----BEGIN CERTIFICATE-----\n...\n-----END CERTIFICATE-----",
"backend_mqtt_endpoint_host": "broker.example.com",
"backend_mqtt_endpoint_port": 8883,
"backend_mqtt_private_key": "-----BEGIN RSA PRIVATE KEY-----\n...\n-----END RSA PRIVATE KEY-----",
"backend_mqtt_use_tls": true,
"gateware_license_key": "abcd="
}
Microsoft Azure IoT
Click to Expand gateware.json: Azure IOT Hub - DPS Group Enrollment
{
"backend_azure_dps_group_enrollment_registration": true,
"backend_azure_dps_scope_id": "0ne00000000",
"backend_azure_sas_primary_key": "000000000000000000000000000000000000000000000=",
"backend_azure_sas_secondary_key": "000000000000000000000000000000000000000000000=",
"backend": "azure",
"gateware_license_key": "abcd="
}
Click to Expand gateware.json: Azure IOT Central - Device Connection Group
{
"backend_azure_dps_scope_id": "0ne00000000",
"backend_azure_dps_group_enrollment_registration": true,
"backend_azure_sas_primary_key": "000000000000000000000000000000000000000000000=",
"backend_azure_sas_secondary_key": "000000000000000000000000000000000000000000000=",
"backend": "iotcentral",
"gateware_license_key": "abcd="
}
3. Install GATE-Ware on your Conduit
There are three options for installing GATE-Ware on your Conduit. Each may be more or less suitable depending on your particular need.
For example, you may decide to use Direct (SSH) for installing during iterative development or manufacturing.
For deployed units, DeviceHQ may be the best option - this method can also be used for converting already deployed Conduits to using GATE-Ware.
Direct (SSH)
The included install-to-conduit.sh script will install the GATE-Ware distribution to the Conduit and automatically start the main application. The script will also configure the Conduit to automatically run GATE-Ware on boot.
- Double check that you’ve created your configuration file:
gateware.json. See section: Create a Configuration File above.
- Copy the
gateware.json file to the gateware/config directory in your GATE-Ware distribution.
- Substituting your credentials and Conduit IP address, use the following commands to install GATE-Ware to the Conduit:
% export CONDUIT_USER="admin"
% export CONDUIT_PASS="ExamplePassword123"
% ./install-to-conduit.sh gateware 192.168.2.1
Direct (Conduit Web Interface)
- Double check that you’ve created your configuration file:
gateware.json. See section: Create a Configuration File above.
- Copy the
gateware.json file to the gateware/config directory in your GATE-Ware distribution.
- Use the following command to create a GATE-Ware distribution archive:
cd gateware
tar --hard-dereference -hczf ../gateware.tar.gz *
- Browse to the Conduit’s web interface and navigate to the
Apps page.
- Click the
+ Add Custom App link on the top-right of the page.
- Enter the following information:
- App ID: GATE-Ware
- App Name: GATE-Ware
- Choose File: Select the
gateware.tar.gz file you created in step 3.
DeviceHQ
- Double check that you’ve created your configuration file:
gateware.json. See section: Create a Configuration File above.
- Use the following command to create a GATE-Ware distribution archive:
cd gateware
tar --hard-dereference -hczf ../gateware.tar.gz *
- Navigate to the DeviceHQ Developer Page and log in.
- Click the
+ Upload App button on the top-right of the page.
- Choose File: Select the
gateware.tar.gz file you created in step 2.
- Click the
GATE-Ware app in the list of apps.
- Click the
Configuration tab.
- Click the
+ Upload Configuration button.
- Click the
Choose File button and select the gateware.json file you created in step 1.
- Enter a helpful description for the configuration file.
- Navigate to the DeviceHQ Device Page and select the Conduit you want to install GATE-Ware on.
- Click Schedule -> Install App -> GATE-Ware.
- Choose the App Configuration you uploaded in step 9.
The next time your device checks into DeviceHQ, GATE-Ware will be installed and start automatically. You can also force a check in to shorten the wait time.